14 Cybersecurity
As tourism firms embrace smart technologies they become increasingly vulnerable to security risks (Paraskevas, 2020). Cyber-attacks are highly damaging to customer trust and the reputation of firms, not to mention the serious financial and legal consequences that can result. Kaspersky Lab (2018) estimates that firms pay an average of US$551,000 to recover from a security breach (US$38,000 in SMEs). These are direct losses only, that is, the money firms must spend on IT recovery services, business losses and downtime, as well as legal and PR services. Indirect losses or the costs of hiring and training additional staff, infrastructure improvements, etc., are estimated on average at US$69,000 (US$8000 in SMEs). Sometimes there are even fines to pay. Data breaches in the Wyndham Hotels and Resorts computer network between 2008 and 2010 compromised the records of more than 600,000 guests with US$10.6 million in fraudulent credit card charges. The event led to a lawsuit from the US Federal Trade Commission in 2012 and from a shareholder in 2014. Both lawsuits were settled for undisclosed amounts. Many other high-profile tourism firms have made negative news headlines because they did not pay adequate attention to these risks and came under attack from cybercriminals, some examples include Marriott, Hyatt, MGM Resorts, Carnival Cruise, British Airways, and Cathay Pacific. This happened because, despite the warnings they received from the ICT industry, they adopted a fragmented and clearly insufficient cybersecurity approach.
Deliberate cyber-attacks are becoming more frequent and their impact has drastically changed from paralyzing the operations of organizations to threatening the security of more critical tasks, such as medical care for a patient or the financial viability of a firm (Reagin & Gentry, 2018). The firms’ response to this new threat environment has been quick to materialize: firms are spending huge amounts of money on cybersecurity. In 2004, the global cybersecurity market was worth US$3.5 billion and it is expected to grow to US$155.83 billion in 2022 and reach US$376.32 billion in 2029 (Forbes Business Insights, 2021). Cybersecurity is no longer an option, it is a strategic asset that every organization must address to ensure business continuity, even more so in the new era of smartization. Cybercriminals are continually improving their techniques and escalating their attacks with higher levels of sophistication, thus causing damage that has more impact for organizations. For this reason, and since preventing cyber-attacks is increasingly difficult, tourism firms need to approach cybersecurity decisively and strategically, quickly adapting information security and developing cyber defense programs that are up to the challenges that lie ahead.
14.1 Cybersecurity in Tourism
Despite the billions spent on cybersecurity, cyber-attacks are considered the biggest threat to the deployment of smart technologies around the world. Furthermore, the travel and tourism sector is specifically one of the sectors most susceptible to cybercrime; the hospitality sector ranks third in terms of the number of security incidents, only behind retail and financial firms (Trustwave, 2020). With the size of the global online travel booking market projected to reach US$2 billion by 2028 (Facts and Factors, 2022), cybersecurity threats can only grow. Customer data stored on countless computers, servers, and networks in hotels, airlines, car rental and reservation firms, and even in bars and restaurants, is a juicy steak for cybercriminals around the world.
Most international hotel groups, from Marriott and Starwood to Wyndham, Intercontinental, Hyatt, Rezidor, Mandarin Oriental, and Omni, as well as smaller independent hotels, have been victims of cyber-attacks multiple times in recent years. But also other firms in the tourism sector such as in airlines (e.g., Air Canada, British Airways, Cathay Pacific, Delta), tour operators (e.g., Thomas Cook), travel websites (e.g., Expedia, Orbitz, Rail Europe), third-party booking platforms (e.g., Sabre Hospitality Solutions), holiday camps (Butlins), trade travel groups (ABTA), chain restaurants (e.g., Arby’s, Checker and Rally’s, Cheddar’s), and even bakery-cafes (Panera Bread), to name a few. They have all been hacked in the last few years and many of them not just once (Paraskevas, 2020). Analysis of data breaches and attacks suffered by tourism firms shows that they are highly vulnerable to cybercrime due to the millions of customers who interact with them in cyberspace, weak defenses at points of contact and sales, and the inherent complexity of travel booking and payment networks, which involve a large number of actors and third-party service providers in a distributed scheme. As a result, even substantial cybersecurity investments often yield very low returns, leading to a “cyber paradox” that involves entering an endless cycle of massive cybersecurity spending with no evidence of security risk reduction.
Many times what really fails in tourism firms is that owners and managers think that cybersecurity is only about implementing a technology, and forget that it is also about training people and (holistically) guiding processes, technologies, the culture, and the physical environment towards the same goal, which is to achieve organizational security. Tourism organizations must create a digital environment that is secure for their employees, customers, and suppliers, and ensure that they will resist in the event of an attack. That is why they need to adopt measures to prevent and respond to cyber threats by adopting an approach based on risk measurement and management.
14.2 Types of Cyber-Attacks
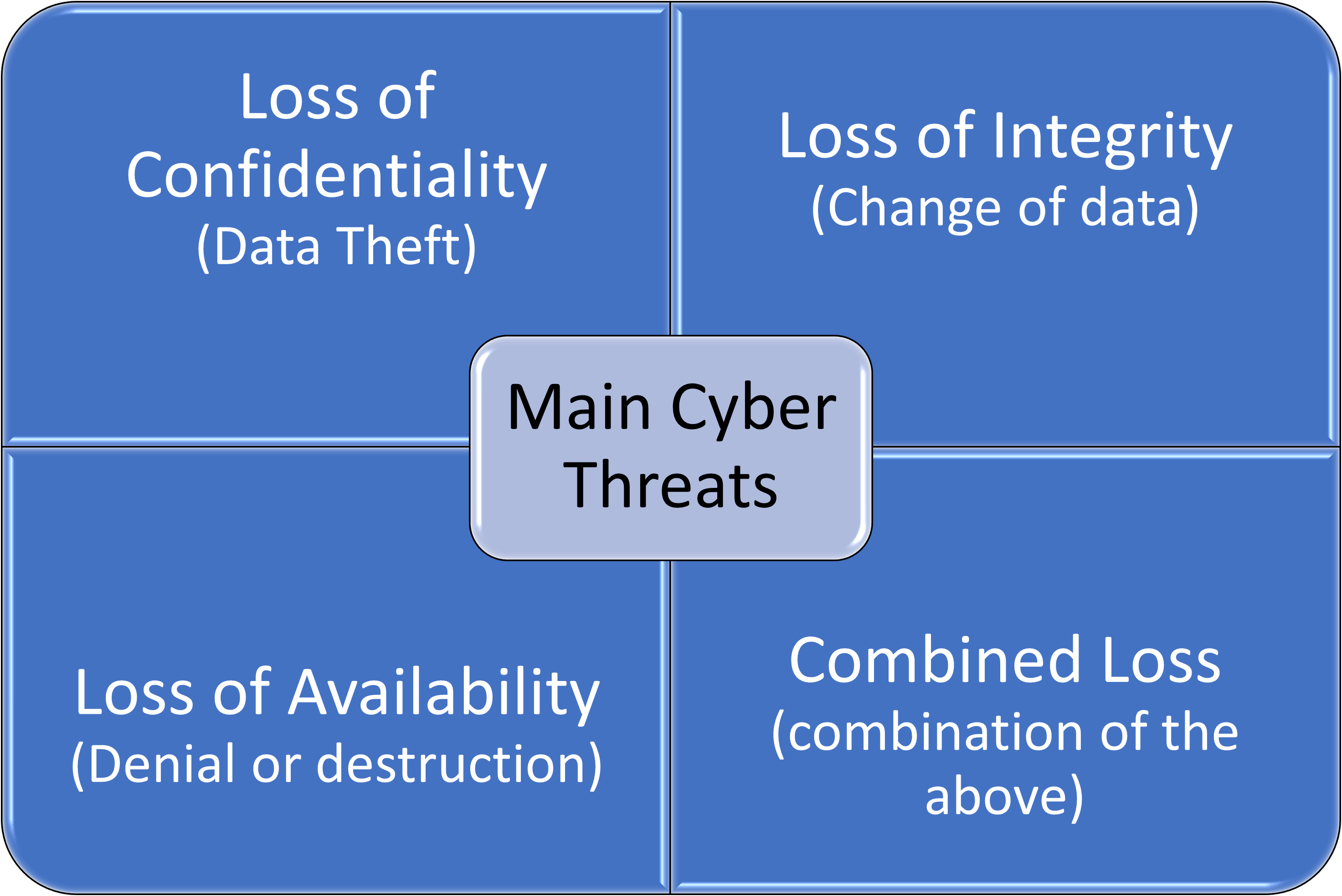
Cyber-attackers employ a wide range of attack techniques to circumvent the cybersecurity measures put in place by firms to protect their systems and data. Most attacks involve high-level technical skills in programming to detect network and organizational security vulnerabilities and inflict damage on organizations, or earn money for data theft or to recover and return to normal (Fig. 14.1). Next, in this section, some of the most frequent types of cyberattacks that occur in tourism firms are examined (Paraskevas, 2020).
14.2.1 Malware attacks
This is perhaps the most common type of attack and involves compromising an organization’s sensitive data and systems by infecting them with malware such as viruses, worms, Trojan horses, keyloggers, and other spyware. There are literally thousands of different malware variants that, once they infiltrate systems and hardware, spread to other systems leaving a trail of disruption and destruction. These attacks typically use a command and control server that allows cyber-attackers to communicate with infected systems, leak sensitive data, and even remotely control the targeted device or server. In the case of tourism firms, one of the most typical types of malware is the Carbanak/Anunak attack.
14.2.2 Point-of-Sale attacks
Point-of-Sale (POS) attacks are a very common type of malware among tourism firms, whereby cyber-attackers obtain valuable data, including the identity of credit card holders, card numbers, and personal identification numbers (PIN). For example, when a customer pays at a point of sale with a credit card, personal and transaction data is temporarily stored in the RAM of the POS terminal while it is transmitted to the payment processor. If a cyber-attacker has managed to install some type of malware on the payment terminal, they can copy the card data and transfer it to an external server. Many hotel groups (e.g., InterContinental, Mandarin Oriental, Radisson) and restaurant chains (e.g., Arby’s, Checker and Rally’s, Cheddar’s) have suffered from these types of attacks, most of which have resulted in customer data being leaked through their POS systems.
Although the number of methods used by cyber-attackers is large, they typically look for vulnerabilities in external systems by injecting SQL into a web server or finding a computer on the internal network that is still using the manufacturer’s default password. Alternatively, they may identify someone within the organization through a spear-fishing campaign or find a vulnerability among digital service providers (usually the weakest link in the chain) to be their gateway. Legacy systems that have not been updated with the latest security patches or are completely out of date are sometimes easy targets for cyber-attackers to infect with their malware. Another variant in the sector is the attack on mobile travel applications through which cyber-attackers can steal the personal data of mobile application users.
14.2.3 Ransomware attacks
The goal of this attack is not to steal data, but to deny access to the owner’s data. While other types of malware have a harder time monetizing (i.e., the stolen data has to be first extracted and bundled and then sold on dark web forums or marketplaces), the goal of a ransomware attack is to make the target pay the attacker directly to regain access to data. The ransomware identifies the most sensitive or valuable data for the organization, corrupts the backups to the point of making them useless, creates backdoors to continue facilitating future infiltrations, encrypts the data and then sends the victim a message with some ransom conditions, usually the payment of an amount in cryptocurrency. It is quite common for firms that are the target of these attacks not to disclose them for fear of retaliation and the impact the attack may have on their brand image, and if they do, they usually deny having paid any ransom. Given the unpredictability of these attacks and the negative repercussions they have for the business, many firms take out insurance that protects them from these cyber-attacks. There are many firms that even have cryptocurrency reserves to cover demands in case of ransomware attacks.
14.2.4 Botnet/Distributed Denial of Service attacks
Botnet/Distributed Denial of Service (DDoS) attacks use thousands or even millions of computers or smart devices (called botnets or “zombie armies”) connected in networks to conduct massive spam attacks, malicious login attempts, or bring down networks, devices, or websites. Some computer or devices are pre-infected with some type of malware, enslaving them so that they can be controlled by cyberattackers and thus have access to the computing power they need to launch these attacks. Once the attack is started, the botnets send large numbers of requests/ queries ranging from simple pings to mass emails. The sheer volume of traffic flowing to attacked networks, devices, or websites literally blocks the capacity of the targeted network or server to the point that other legitimate users cannot access or are denied access. The objective aimed by these attacks is to interrupt normal business operations or degrade the level of service of the organizations targeted by the attack, which is why they are also known as Distributed Denial of Service attacks. Many tourism websites are attacked in this way causing further slowdowns and downtime of networks and websites, and even increased GDS transaction costs when attackers ravage ticket sales.
14.2.5 Wi-Fi/website compromise
Cyber-attackers are good at hitting unsecured public networks in hotels, cafés, airports, visitor centers, etc. to infiltrate tourists’ devices, infect them with their malware, and steal personal data, or use them as unintentional insiders for their next targets. In addition to exploiting Wi-Fi vulnerabilities, cyber-attackers also use a technique known as the “evil twin” attack, which consists of locating near a genuine Wi-Fi access point (i.e., the public Wi-Fi network of a tourist office) and discovering its Service Set Identifier (SSID) and frequency. Once this information is obtained, they send out a radio signal using the same frequency and SSID that appears to visitors as legitimate access with the same name. By the time visitors connect to the “evil twin”, cyber-attackers have already taken control of the device, so all they have to do is collect personal data and start monitoring every activity that takes place on the device. “Evil twins” are also known as “honeypots” or base station clones and are very common threats in the travel and tourism industry.
Tourism firm websites are another attack vector through which to steal valuable customer data, including payment data. The websites of major hotels, museums, and transportation firms often provide detailed information about guest reservations, including reservation code, name, address, telephone number, last four digits of credit card, etc. to third party advertisers, social media, and other partners. Cyber-attackers can access and use this data to log in to a reservation, view personal details, and even modify or cancel the reservation.
14.2.6 Cognitive hacks
The continuous improvement and sophistication of cybersecurity defense systems has led many cybercriminals to review their tactics and focus on easier targets: the weak points of the human mind. Unlike regular cyber-attacks where cyber-attackers exploit vulnerabilities in IT systems, cognitive hacks are designed to exploit people’s psychological vulnerabilities, using deception to manipulate their perception and circumvent security. Phishing is the most common type of cognitive attack and involves massive email campaigns that attempt to trick employees of organizations into downloading attachments containing some form of malware or providing their login details. Another more sophisticated tactic is spear-phishing, which targets specific members of staff or specific roles, and tries to make them believe that the malicious email they are receiving has originated from a legitimate source. A large number of hotels and guest houses listed on online booking platforms have been targeted by phishing campaigns in recent times. Customers of these platforms receive emails that appear to come from a legitimate source asking them to provide payment details and personal information such as name, address, phone number, etc. Other times, users are asked to log in to their accounts or sign in to troubleshoot a technical issue.
To anticipate the movements of cyber-attackers, it is important to understand not only the hacking techniques they use, but also the reasons that move them to act and the prize they can achieve. Not all cyber-attackers think the same or follow the same methods as defenders, so defenders must be open-minded and interdisciplinary in order to foresee various defense techniques. It is important that the people in charge of providing cybersecurity solutions in the tourism firm periodically try to answer the following questions to predict or try to anticipate the next move of cyber-attackers:
What are the most critical assets of the organization, the most vulnerable, and the most damaged if they are attacked?
How can the firm protect its access points?
By what methods can cyber-attackers gain access to the firm’s “crown jewels”?
Where are the “crown jewels” located? Do they have sufficient protection measures to repel a cyber-attack?
Is there an updated inventory of authorized devices and the level of access granted?
What kind of malware defenses are being used by the firm? What defenses are planned?
How effective and robust are the intrusion detection systems used by the firm?
How is the firm notified of a potential threat or breach? Is there a plan to combat the insider threat?
Are operating systems of the firm properly configured and up to date? What about the rest of the software installed on the computers owned by the firm?
Is there a process or system to identify stolen credentials or compromised user accounts?
Are employees aware of the risks of cyber-attack in the firm? Do they receive any kind of training or awareness program on the subject?
Source: Own elaboration based on Maalem Lahcen et al. (2020)
14.3 Cybersecurity in SMEs
One of the main problems of tourism SMEs with cybersecurity is that they tend to underestimate the threats they face, thinking that cybersecurity is not an issue they should worry about but something more typical of large firms, since their assets are much more lucrative for cybercriminals. This attitude is unprofessional and shows little knowledge of the subject. Quite often the result is a headache for the organization and its stakeholders.
SMEs have become one of the most valuable targets for cybercriminals. In most cases, the techniques used by SMEs to defend themselves are weak and involve little experience, inferior skills, and old or weak security methods. It does not matter that SMEs think that they have few assets with no apparent value for cybercriminals, it is enough that they are suppliers or partners of a larger business group to become a target through which cybercriminals will seek to catch the biggest fish. If we add to this the fact that they have fewer resources to defend themselves and are not willing to take costly legal action against cyber-attackers, SMEs are more attractive to many cybercriminals who see them as easy prey that they can attack without serious consequences.
Currently, poor risk management and the lack of adequate and sufficient measures to protect against cyber-attacks have become major issues for SMEs. This means that SME business strategies often pay less attention to risk management implications, which can have very unfortunate consequences affecting both tangible and intangible assets or, worse yet, lead the firm to bankruptcy (Alahmari & Duncan, 2020). SMEs are more likely to adopt a low-cost cybersecurity approach with a minimal cybersecurity budget and very basic standards far from their strategic priorities, thus becoming more vulnerable to cyber-attack threats. The development of cybersecurity practices as a key strategic factor of the SME could be a solution that would save owners and managers a lot of trouble and mitigate risks. For example, strengthening employee cybersecurity training is an important factor in improving their behavior within the organization and preventing them from being the cause of many of the cybersecurity threats that affect SMEs (i.e., when they ignore policies on information management and access to information). Other times, it will suffice to implement the practices contained in the General Data Protection Regulations (GDPR) and carry out campaigns that make the organization’s decision makers aware of the consequences of a bad cybersecurity policy and the need to invest more to reduce the biggest cyber risks.
Today the use of IT technologies that are reliable and secure is a crucial factor in supporting the growth of tourism SMEs in the context of the Smart Revolution. Owners and managers should keep in mind that when cybercriminals identify vulnerabilities in the systems of an SME, attacking them will become their top priority, and they will not hesitate to exploit them sooner rather than later. Therefore, without technologies that are reliable enough, up-to-date, properly integrated into a managed IT framework, and well protected from the threats that surround them in cyberspace, cybercriminals will exploit the disadvantages and inflict serious damage that will cost a lot of time and money to repair. At the end of the day, it is not “if” the firm will one day be the victim of a cyber-attack, but “when”; therefore, leaders must strive to adopt a risk-based approach that allows them to defend their organization from all kinds of cyber-attacks.
14.4 Key Challenges in Cybersecurity
Stories of cyber-attacks have become routine, with cyber-attackers showing increasing levels of sophistication and damage inflicted. The race to discover new ways to exploit weaknesses in the defenses of firms’ IT systems does not stop, so it is important that owners and manager are aware of the magnitude of the challenges they face and understand what is at stake. Below are some of the most important challenges that every tourism firm must know about to ensure the security of its operations in cyber space.
14.4.1 What matters most?
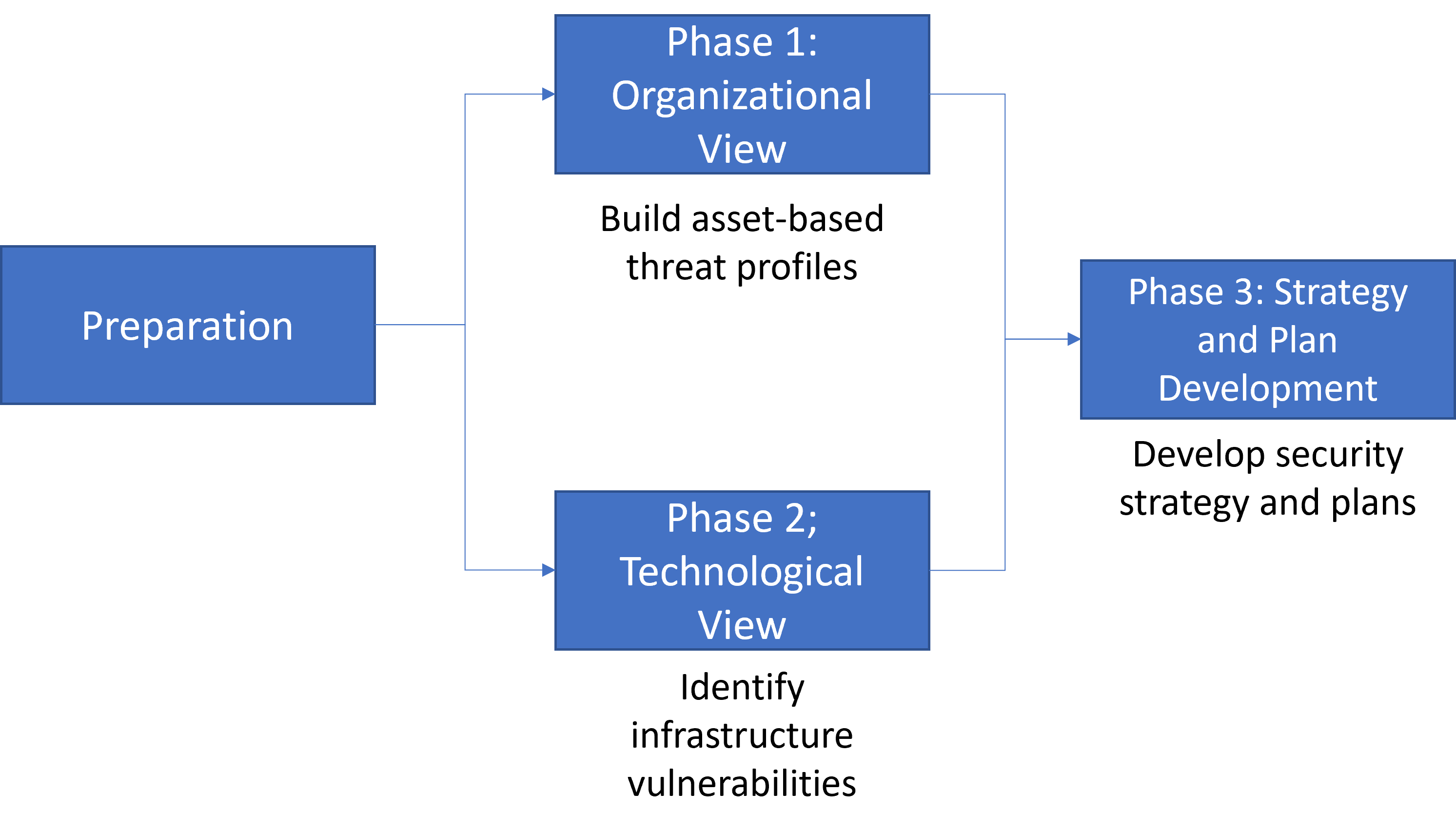
A cybersecurity strategy must provide the best possible protection for the key assets and operations of the firm. In this vein, organization must understand which IT systems are mission critical for its operations, as well as being clear about which information assets are the most valuable to cyber-attackers in order to apply enhanced protection to them. In addition, the firm must know where are and who has access to critical assets, and know how these assets are related to each other and what vulnerabilities (organizational and technological) can expose them to cyber-attackers. This process is known as OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) and is a methodology for evaluating information security risks that allows establishing a set of risk profiles for critical information assets and systems (Fig. 14.2). These profiles will allow business owners and managers to make informed decisions about the allocation of resources that strengthen the organization’s cyber defenses and implement an adequate cybersecurity strategy for the firm (Caralli et al., 2007).
14.4.2 Risk management frameworks
Tourism firms must properly manage risks if they want to succeed in cybersecurity, so choosing a risk management framework from the many available on the market is an essential task. One of the most popular cybersecurity frameworks is the US National Institute of Standards and Technology (NIST) Cybersecurity Framework. This is a high-level, easy-to-read set of guidelines for mitigating organizational cybersecurity risks, which organizations can customize to suit their needs. The framework consists of a core divided into five functions (identify, protect, detect, respond, and recover) further subdivided into 23 categories. For each category, a series of subcategories of cybersecurity results and security controls are defined, with 108 subcategories in total.
ISO/IEC 27005 is another good option for tourism firms. It is a set of standards developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) that provides owners and managers with system-wide guidelines and techniques for implementing and managing information security risks in the organization. With the ISO/IEC 27005 standard, firms can acquire the ability to identify, analyze, evaluate, and treat various risks to information security, as well as prioritize risks and take appropriate actions to mitigate them. Firms that wish to improve their information security management systems do not need to apply the entire methodology of the standard but can focus on a series of factors such as the information security risk assessment, or the information security risk treatment.
Firms may also decide to use the OCTAVE methodology, a framework developed at the CERT(R) Coordination Center of Carnegie Mellon University in the United States widely used by organizations of all kinds to assess cybersecurity. OCTAVE helps organizations identify and classify key IT assets, assess threats to those assets, analyze their vulnerabilities and impacts, and develop security priorities that help reduce IT asset risk. At the core of OCTAVE is the concept of self-direction whereby a small interdisciplinary team of people from within the organization’s departments take responsibility for directing the assessment process and setting the organization’s security strategy.
The CMMI Institute has developed the Cybermaturity Platform, which shares a risk management approach similar to that of OCTAVE. It is a proactive, evidence-based cybersecurity approach to assess, optimize, and report on cyber capabilities. A distinctive feature of the Cybermaturity Platform is that it allows organizations to prioritize a risk-based roadmap, which is a personalized list of actions based on the most relevant cybersecurity risks that have been identified.
Global security and aerospace company Lockheed Martin has also developed the Cyber Kill Chain framework, which is part of the Intelligence Driven Defense model for identifying and preventing cyber intrusion activity. The model consists of seven steps through which the organization identifies what cyber-attackers would do to achieve their goals, thus enriching an analyst’s understanding of an adversary’s tactics, techniques, and procedures. The model proposes the measures that the defender must take to break the “chain” at an early stage, as well as at later stages.
14.4.3 Security of data and IoT
Data cybersecurity is an unavoidable problem that must be seriously addressed by all tourism firms transitioning towards smartization. If the problem is not adequately addressed or resolved effectively, cyber-attackers will exploit flaws and weaknesses in the organization’s data systems to hijack them, distort data, or simply disrupt the organization’s service. The damage inflicted by an attack on the firm’s data will far outweigh any gains the firm has previously made.
Cybersecurity attacks are occurring at unprecedented levels on IoT systems and are causing a variety of significant issues for people and having damaging consequences for the reputation, compliance, finances, and operations of tourism firms. Furthermore, according to data provided by a recent survey, IoT-based threats have become a major problem: 8 out of 10 firms have suffered some type of cyberattack on their IoT devices in the last 12 months, and 26% of organizations that had been attacked were not even using security protection technologies (Irdeto, 2019). This increase in the level of threat to IoT systems is due in part to the phenomenal growth of IoT devices and technologies. As the number and variety of connected devices in IoT networks grows, security threats grow exponentially. Advances in 5G and related IoT developments are expected to make cyber-attacks even more common. This highlights the sheer magnitude of the threat and points to the need for tourism firm owners and managers to understand cyber risk management processes and be proactive in investing in IoT cybersecurity.
The purpose of IoT cybersecurity is to reduce the risk of a cyber-attack for users and organizations operating in the ecosystem through the protection of IoT assets and data privacy (Lee, 2020). Due to the dynamic and temporary nature of the connections between IoT devices and the diversity of actors acting in IoT systems, this is undoubtedly a big challenge for firms operating an IoT system. Furthermore, traditional security protocols and mechanisms are no longer adequate, and new methodologies and technologies are needed to meet IoT security, privacy, and reliability requirements.
The very complexity of IoT architectures is another factor that makes it difficult to defend against attacks, as each layer of the IoT architecture has its own challenges and security issues that are unique and interact with other layers. This requires dealing with security measures in a holistic way for the entire IoT architecture and not for any specific layer. Fortunately, the cybersecurity industry is very dynamic and new cybersecurity technologies are continually emerging that provide greater opportunities to withstand attacks unscathed, but also bring with them new challenges for managing IoT cybersecurity risks that organizations must prepare for.
Despite the significant investments that are being made in cybersecurity, owners and managers should keep in mind that there are still no standards that can help them choose the most appropriate cybersecurity technologies. This becomes particularly evident when it comes to deciding on cybersecurity solutions that must protect systems that handle large amounts of data (i.e., IoT), and for which there is an urgent need for secure products and services.
There are currently three open lines of work focused on achieving a security standard in the IoT, to which managers of tourism firms will have to pay attention in the coming years to see the results. These efforts are carried out by the Global Standards Initiative on Internet of Things (IoT-GSI) of ITU-T, the ISO/IEC JTC 1/SWG 5 IoT of the Joint Technical Committee ISO/IEC JTC 1 of the ISO and the IEC, and the TS 103645 standard of the European Telecommunications Standards Institute (ETSI) for the security of internet-connected consumer devices and their associated services.
14.4.4 Hackers’ behavior
Since most cyberattacks are human-caused, it’s important for cybersecurity managers at firms to understand who these criminals are, why they do what they do, what they’re after, and how they operate. Knowing the behavioral aspects surrounding cyber-attackers is very useful to better understand the challenge facing the organization and try to align the behavioral aspects with the technical aspects of cybersecurity. For an organization to understand what its cyber risk landscape looks like, it suffices to consider that cyberattacks are broadly classified into three main categories: war, activism, and crime. In other words, hackers have geopolitical, ideological, and financial motivations, and can be sponsored by states, be activists, or be criminals (Paraskevas, 2020). Figure 14.3 shows the cyber-risk landscape, that is, the connection between the types of hackers, the threats that occur, and the type of impact they can have on businesses.
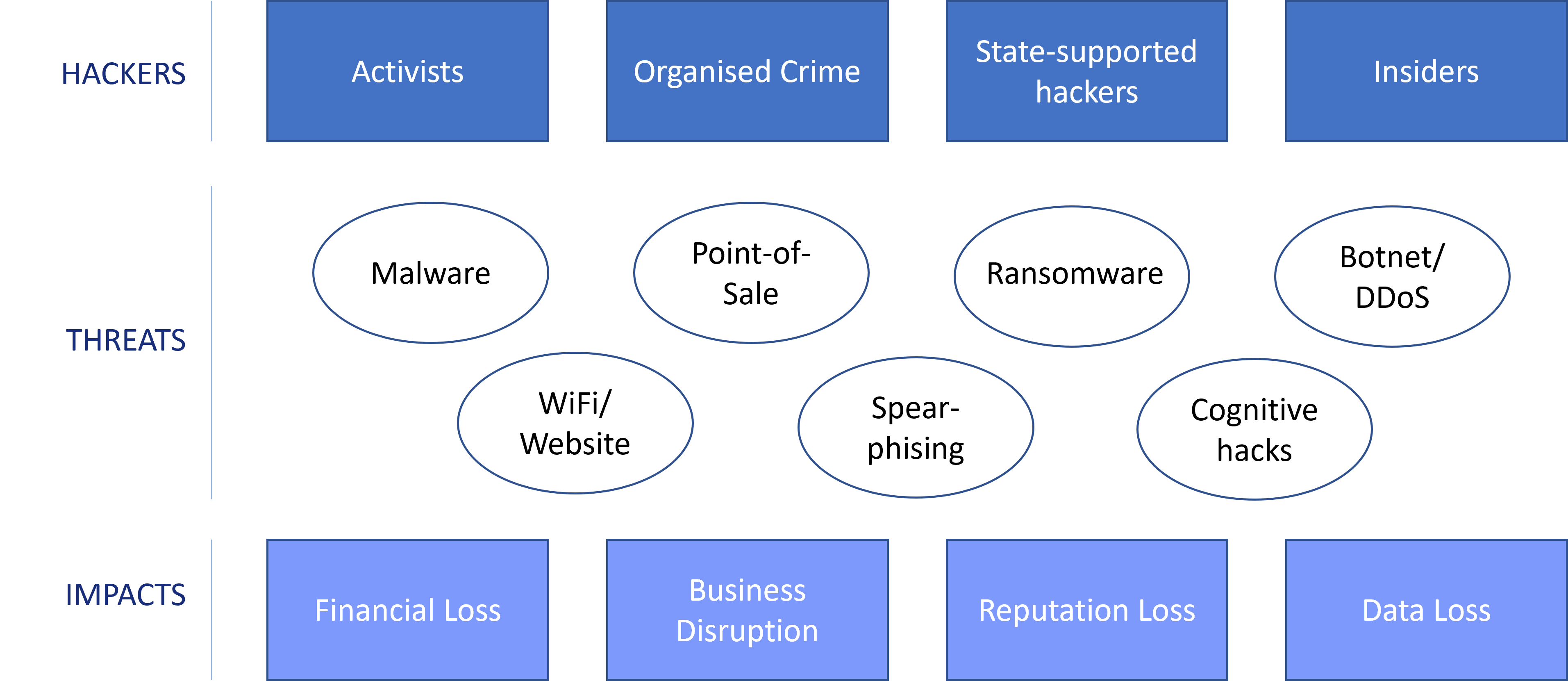
There is no IT system that is 100% secure, but it is also not possible to maximize security without considering the human factor. In general, cyberattackers will attempt to penetrate all levels of the organization’s defense system after having gained access to the first level. Consider that it takes most hackers an average of 15 hours to gain access to an organization’s system and map and detect its most valuable data to compromise it (Pogue, 2018). There is no doubt that cybercriminals have an advantage over defenders, which is why defenders are obliged to analyze security at all levels using tools that allow them to discover vulnerabilities before attackers do. Here the famous slogan “Trust, but Verify” (which became internationally famous when it was used by US President Ronald Reagan in the context of negotiations on nuclear disarmament with the Soviet Union) is perfectly valid, which means that even if the firm achieves a certain level of trust in some domains of the organization, it will always be necessary to carry out continuous verification.
14.4.5 Insiders
An insider is a hacker within the organization who has access rights, privileged information, and is behind firewalls. The threat of insiders has long been recognized as a major problem for the management of cybersecurity in organizations (Theoharidou et al., 2005). The Insider Threat Spotlight report indicates that firms are more concerned about data breaches stemming from unintentional insider threats than malicious data breaches (Information Threat Group, 2017). According to this report, 74% of organizations feel vulnerable to insider threats, albeit 42% have adequate controls in place to avoid an insider attack. Privileged users, such as administrators who have access to sensitive information, pose the greatest internal threat to organizations, followed by contractors, external consultants, and regular employees. Most security professionals confirm that insider threats have become more persistent in the last 12 months and that they expect their budget to deal with these threats to increase over the next year. Moreover, 75% of organizations estimate that internal violation remediation costs could be as high as US$500,000.
A troubling issue is that organizations often do not want to admit that they experience internal incidents of this type, preferring instead to fire the insider and protect their reputation. Nonetheless, insiders exist and are more frequent when there are disgruntled employees in the organization, people who suffer stressful events (i.e., sanctions), or people who are prone to this type of behavior (i.e., drug use, aggressiveness, etc.). Sometimes these issues are the result of unintentional human error (lack of knowledge or operational skills), intentional error (misuse of assets), or malicious behavior (with the intent to cause specific harm).
14.5 Success Factors
Any successful cybersecurity program should consider three related factors: people, processes, and technologies (Reagin & Gentry, 2018). Many organizations emphasize the technical components of their program, such as firewalls, intrusion prevention systems, and vulnerability scanning. However, the responses that tourism firms should give to the problem of cybersecurity must address much more than the technical components. We discuss below how each of these factors should be considered.
14.5.1 People
It is vital that organizations form a cybersecurity team and have a professional management framework dedicated to cybersecurity risk assessment that the team can align with at all times. This requires harnessing the leadership of the firm’s executive team to develop robust risk management processes and empower all firm personnel through ongoing training. It is important that senior management view cybersecurity as an organization-wide issue and mobilize all employees to be accountable for risk management and oversight of cybersecurity as they would do with any other significant risk to the organization. Establishing an information security oversight committee, chaired by the firm’s CEO or COO and involving executives from all business units of the firm, is a proven best practice in many organizations. The committee should meet regularly to review newly identified cybersecurity risks and update security policies and procedures.
The development of a cybersecurity program naturally requires qualified personnel to take on new tasks. It will not be an easy task for a tourism firm, especially when it is an SME, to find the right personnel with which to launch a cybersecurity program given the current high demand for this personnel and the shortage of professionals. Another option available to SMEs is to partner with a Managed Security Service Provider (MSSP) and create a hybrid team (i.e., combining internal and partner resources to bring together the key components of a security program, rather than developing the program completely themselves). This will help the firm gain agility as well as reduce costs.
Once the team is formed, establishing the right links between people, processes, and security technologies is another key success factor for the organization’s cybersecurity program. This is the time when the cybersecurity team will need to decide on the cybersecurity framework to use (e.g., NIST, ISO/IEC 27005, OCTAVE). The chosen framework should allow the team to document and assess its ability to prevent, detect, and respond to cyber-attacks, while applying good cybersecurity practices that integrate both a compliance-based approach and promote anticipation through proactive threat behavior. The selection of the key controls to be implemented in the firm is an important step that must be decided based on the probability and impact that the threats may have, even more so considering the large number of providers that currently exist and the large number of technical controls that are available.
14.5.2 Processes
The process framework establishes the model to be followed by the organization’s cybersecurity program. It contains the set of policies, rules, and procedures to be followed by the organization that guarantee that the cybersecurity measures and tools will be used consistently and effectively, and that they will be updated periodically. It also forms the basis for a cybersecurity auditor to examine the firm’s security framework and assess whether the program is achieving its objectives. To evaluate and compare the effectiveness of the cybersecurity processes developed by the organization, the firm should develop key performance indicators (KPI) that focus, among other things, on the following indicators (KPMG, 2015):
The probability and impact of the main threats.
The degree of compliance with internal and external standards.
The metrics from previous security incidents (i.e., the number, business impact and source of serious incidents, average incident detection/response time, etc.).
Cybersecurity awareness and culture indicators (i.e., clarity of rules, exemplary behavior, practicability, visibility, organizational openness, etc.).
The degree of progress of the key security initiatives with respect to the plans.
The level of current threat.
When considering a cybersecurity framework, business owners and managers should keep in mind that excessive application of security controls can also be a drag on innovation, without bringing additional benefits to organizational performance. For this reason, it is convenient to evaluate both the probability and the impact that each security threat has on the organization and thus decide which ones should be prioritized and will require an additional investment for the implementation of technical controls.
14.5.3 Technologies
When it comes to determining which cybersecurity technologies the firm should invest in, owners and managers should try to optimize the elements that make up the organization’s cybersecurity program. Basic controls, such as firewalls and email filters, are essential elements that every tourism firm should have, but there are also other essential components to consider.
Anti-spam/anti-virus software: It remains a vital piece of the cybersecurity puzzle in organizations, especially for blocking known malware on a large scale. However, it is no longer the only component that can be relied upon to keep the business safe from cyber threats. Organizations need to ensure their anti-spam/anti-virus software is always up to date to protect themselves from online threats.
Automated patch management: It is a process dedicated to automatically assessing which updates are critical (and which can be ignored) and applying them to the systems that need them, thus ensuring that risks are not increased by running older operating systems or software.
Perimeter security: It is about using firewalls (network devices that block certain types of network traffic) to protect the organization’s network and prevent unsolicited and insecure traffic. A good firewall must also provide visibility into any intrusion attempts and allow the firm to block access to unwanted websites and applications immediately. The firewall must also support remote access VPN networks to securely allow access to external users.
Data backup technologies: Data backups are the only certain guarantee against data loss. Data loss can be caused by human error, a cyber-attack, or a local disaster such as fire or flood. That is why it is important for the organization to ensure that the heart of its business (its data) is safe and sound no matter what. Once server-level and desktop-level backups are captured, the organization should periodically test them to ensure they are working properly.
Multi-Factor Authentication (MFA) (also known as dual-factor authentication or two-step verification): It creates an additional layer of security that forces cyber-attackers to have not only a username and password to gain access to the system, but also a token to authenticate remotely.
Once the organization has the above controls covered through foundational level technologies, there are much more advanced technologies that tourism firms will need to invest in to counteract the cyber threats that are becoming more sophisticated and damaging. The following advanced security technologies are designed to provide greater visibility and control so the organization can successfully address today’s threat landscape.
DNS security, to prevent the organization’s systems from resolving and connecting to malicious domains.
Managed Detection and Response (MDR), for advanced threat hunting and incident response through continuous visibility.
Mobile Device Management (MDM), so that the organization’s control extends to mobile devices that have access to firm data.
Honeypots, or custom lures that simulate the organization’s data and intellectual property, including spreadsheets, documents and files, etc.
14.6 The Future of Cybersecurity
Traditional cybersecurity strategies and tools have become increasingly ineffective as the cyber threat landscape has continued to grow. Organizations have no other option but to continue responding to the new security needs that are emerging. The mentality of tourism firms regarding cybersecurity will need to change from being mostly reactive to being proactive. Instead of only detecting malware and other types of threats days after they have been installed on the organization’s systems or after they have caused damage, firms will need to actively search for malware and all types of attacks lurking in cyberspace before being activated and causing damage within the organization. This approach that seeks to anticipate threats is already possible thanks to advanced Endpoint Detection and Response (EDR) solutions and AI technologies.
With so many cases of security breaches made public in renowned firm and that have a high media impact, privacy and data protection will become competitive factors to be considered by tourism firms. Those firms that treat cybersecurity as a simple compliance exercise will eventually lose the trust of the market (Paraskevas, 2020). Tourism firms will need to seek solutions that offer flexibility in identity and access management to respond to the increasingly fluid needs of customers. The adoption of as-a-Service models (i.e., IDaaS, PAMaaS) that enable passwordless authentication, single sign-on, and user-friendly multi-factor biometric authentication are options that will greatly facilitate the management of cybersecurity in tourism firms.
Finally, as more tourism firms move their IT infrastructures and data centers to the cloud, it will be essential to adopt a distributed, multi-cloud approach that includes reservation, revenue, call center, channel/distribution, and content management, as it will bring more flexibility, resilience, and cost advantages for the tourism firm. In this vein, two of the main challenges for tourism firms will be: 1) to guarantee compliance with card payment data security standards (Payment Card Industry Data Security Standard, PCI DSS) when personal identification data crosses multiple layers of the cloud; and 2) design an integrated prevention–detection–response strategy automated to threats.
14.7 Discussion Questions
What are the most critical and vulnerable assets of a tourism firm that would be most affected if they were the target of a cyber-attack?
What are considered the “crown jewels” of a tourism firm from a cybersecurity point of view? How are tourism firms protecting attackers’ access to the “crown jewels”?
What non-technological measures can the tourism firm take to better protect itself from cyber-attacks?
Identify a publicly known case of a cyber-attack on a tourism firm and describe what type of damage was caused. Was the viability of the business compromised?
What impact does the adoption of cybersecurity measures have for the firm’s employees and customers? Is there any impact on productivity and/or customer experience?
How should a tourism firm react when it is aware that it has suffered a cyber-attack? What internal and external communication actions should be carried out?
What capacities and professional skills do tourism SMEs currently have to manage cybersecurity processes and decision-making? Are they enough?