13 Internet of Things
The accelerated changes in internet applications and technology are reflected in the development of the so-called Internet of Things (IoT), which describes a global network of connected and integrated devices with ubiquitous computing capabilities. Similar to the profound transformation that the internet has undergone, led first by infrastructure (e.g., fiber optics, routers, Ethernet cables, etc.) and then by business models, the same is happening today with the IoT. Firms and the technology industry are devoting a huge amount of resources to the design and implementation of infrastructure (e.g., sensors, gateways, base stations), but in a few years the focus will radically change towards business opportunities.
The key idea behind the IoT is to interconnect physical “things” through digital communication networks (e.g., via Wi-Fi, Bluetooth, Ethernet) to allow the “things” to exchange information with each other and help the user to make smart decisions for themselves. This ability of the IoT to convert each physical object into a potential digital artifact, a process known as “leak” or “liquification” of information resources, means the transformation of a physical object into a series of information resources that characterize it, on which it is possible to act (Ng & Wakenshaw, 2017). In an IoT context, each physical object is associated with a set of digital data (current and historical) that contains information about its physical properties, the origin, ownership, and the environment, which can lead us to imagine a world in which each physical object can be part of the internet.
IoT ecosystems are going to be central to Big Data collection. In fact, it is expected that the main source of Big Data in the coming years will be IoT systems, followed by data from humans and robots and AI applications (Kaivo-Oja et al., 2015). Through the IoT, firms will be able to track, communicate with “things”, and monitor them to exploit their status. But even more important is that due to the programmability of “things” it will be possible for firms to add new instructions and modify their behavior throughout the life cycle of things (Fig. 13.1). Ultimately, this ability for everyday “things” to think and interact will be the driver of the IoT, unleashing limitless opportunities for tourism firms, most positive and some negative. Therefore, the IoT represents a new paradigm that has the potential to revolutionize the way we live and work thanks to the vast amount of data and services that flow from the interactions between a large number of heterogeneous connected devices (Palattella et al., 2016).
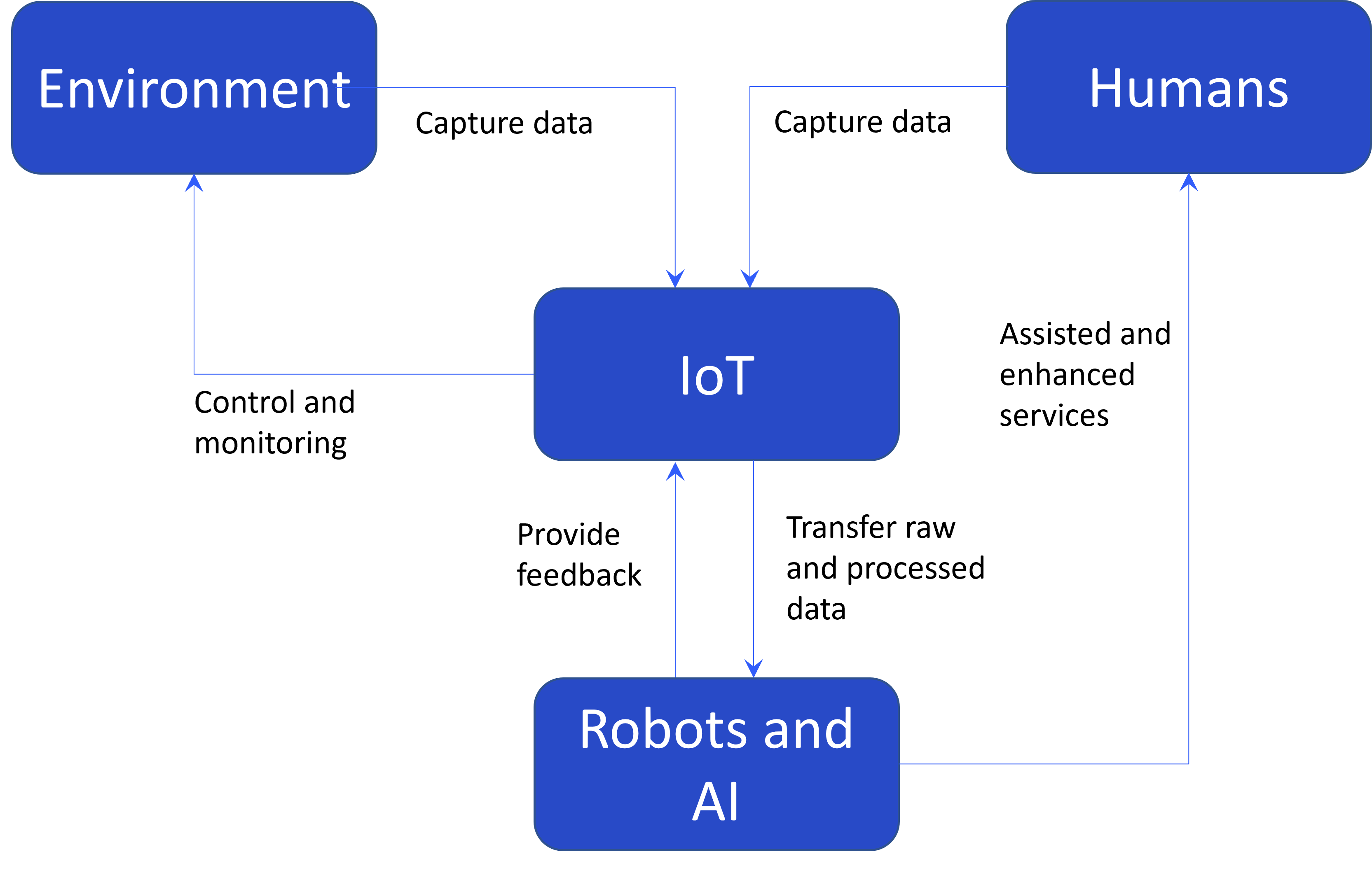
13.1 Concept of IoT
One of the first to use the term IoT was MIT technologist Kevin Ashton, who explained how the IoT could be created by adding radio frequency identification and other sensors to everyday objects (Ashton, 2009). Over time, the term IoT has evolved to refer to a “network of entities that are connected through any form of sensor, enabling these entities, which we term as internet-connected constituents, to be located, identified, and even operated upon” (Ng & Wakenshaw, 2017). Today, the IoT is considered one of the technologies that is going to lead the way to the Fourth Industrial Revolution and that interconnected physical devices will automate skills and tasks, significantly impacting the way consumers, businesses, and governments interact (Shim et al., 2019).
The IoT encompasses a network of physical objects including anything from a smart watch to a critical infrastructure control system. Each object in turn consists of some type of sensor (e.g., temperature, light, movement, etc.) or actuator (e.g., screen, sound, light, motor). Other components of the IoT ecosystem are the embedded technologies to communicate with and sense the surrounding environment and interact with its internal states, such as computational resources to process the data detected locally or remotely, and a shortrange (Bluetooth, ZigBee, radio-frequency identification (RFID)) or long-range (internet) means of communication to transmit the data.
IoT devices detect or read the environment in which they are embedded without human intervention. The data so detected is then processed and analyzed to acquire information and knowledge, which is distributed to those who will decide whether to take any action. Indeed, the essence of the IoT is to make any information available to anyone at any time. This relegates the traditional separation between physical and digital objects to the past (Fleisch et al., 2015), and merges both worlds to create smart ubiquitous services that offer endless opportunities for business and society.
But, one may wonder, why do we need to connect all “things”? The answer seems evident: the IoT is a big step forward towards automating processes that improve centralized control and management (Pramanik et al., 2018). The automation provided by the IoT can reduce operational costs compared to manual tasks, by automatically controlling and managing many independent devices that are connected and communicate with each other. The number and variety of communication technologies is currently so big that the IoT encompasses a great diversity of application domains and almost infinite possibilities for communication and interaction. This is being made possible, among other things, by the reduction in broadband internet costs, advances in wireless network technologies, access to the cloud, the reduction in prices of sensors with detection and communication capabilities, and the arrival of 5G cellular systems. Some forecasts, such as those of the Swedish technology company Ericsson, suggest that there will be around 29 billion connected devices by 2022, of which around 18 billion will be related to the IoT. This will generate trillions of dollars of value for businesses and national economies. The enterprise IoT platform market alone is estimated to reach, according to consulting firm Gartner, US$7.6 billion in 2024 with a compound annual growth rate of 31%, driven by growth in on-premises and cloud solutions in all industries.
For many specialists, the IoT represents the next step in the computer revolution, which will be based on the incorporation of information and communication technologies in home machines, in the workplace, and in a wide range of industrial processes (De Saulles, 2016). The massive interconnection of devices and the incorporation of network sensors in everyday objects will provide tourism firms with unimaginable amounts of data. Moreover, AI and machine learning applications to analyze and make sense of this data will lead to a new wave of innovation in business processes. Together, the IoT, Big Data, and AI will eventually drive a radical reshaping of industries and business models by providing new insights into how business ecosystems and customer relationships work, unlocking new revenue streams through unprecedented use cases. Ultimately, new firms will emerge that are able to harness and capitalize on IoT data, while established firms will need to adapt the way they operate or face extinction, just as they did when steam, electricity, or the internal combustion engine came along and the old ways of working became obsolete.
13.1.1 IoT vs IoE
The IoT is built on the data created by things. This is a significant difference from how the internet has developed up to now, mainly based on data created by people. Building on this idea, some big companies in the technology industry (including CISCO and Qualcomm) have adapted their view of the IoT and used the term “Internet of Everything” (loE) instead. Unlike the IoT, which is made up of “things”, the IoE encompasses four pillars: people, data, processes, and things (Fig. 13.2). In the IoE, devices are permanently connected to the internet, including machine-to-machine (M2M), person-to-machine (P2M), and person-to-person (P2P) systems. This makes it possible for business and industrial processes to be put at the service of improving people’s lives.
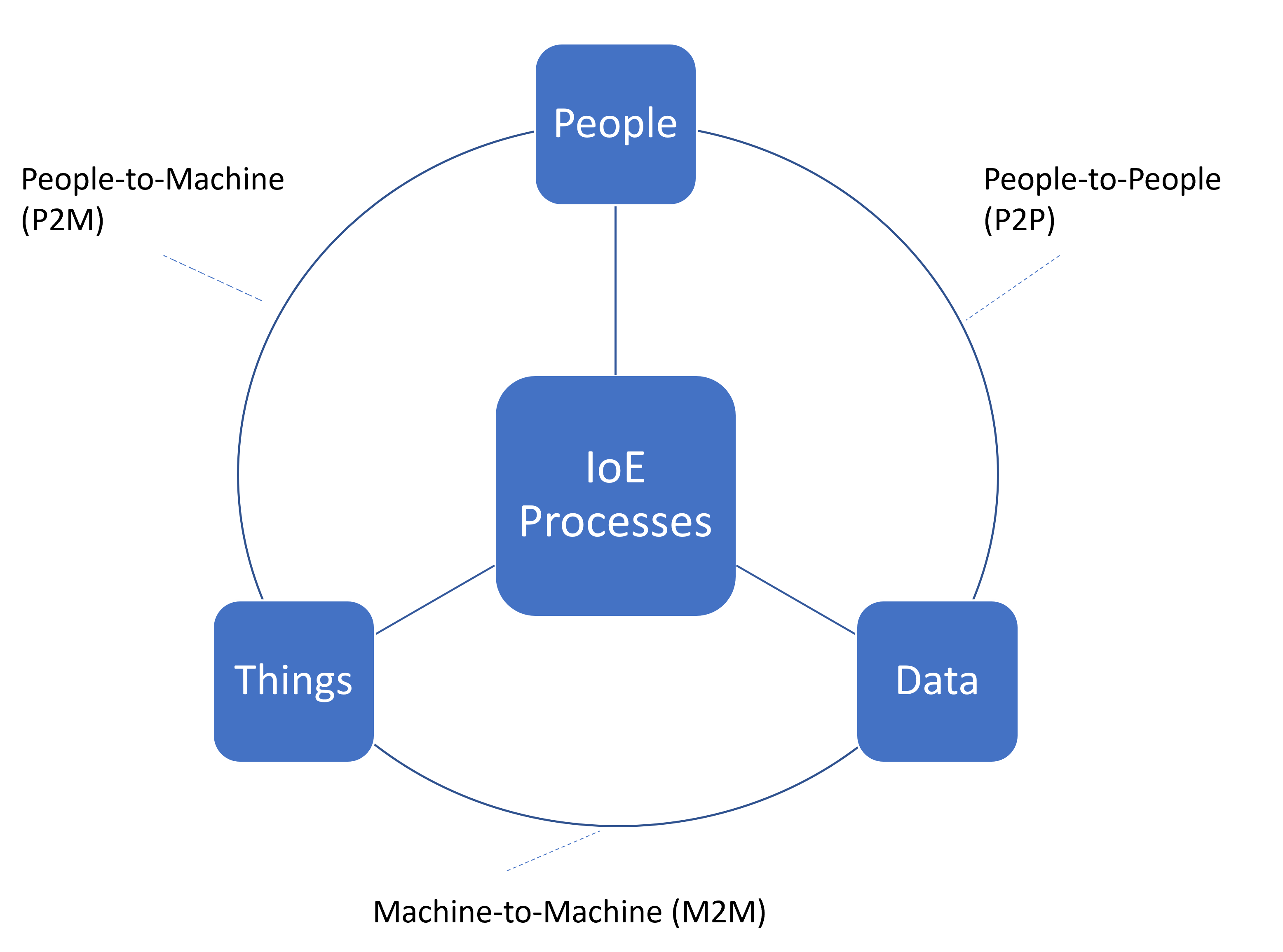
For IoE advocates, the big issue is not so much “things”, but the connections between things, people, processes, and data, which is what really creates value. They believe that the growth of many organizations in the Internet Age occurs in waves that are “S” shaped, such that with each successive wave new features and greater network connectivity are added, eventually leading to qualitative and quantitative leaps in the number and variety of opportunities (and of risks) and firms reaching the IoE.
The IoE offers the potential to extract and analyze real-time data from the millions of sensors connected to IoT platforms that can then be used to optimize human-centric automated processes. For example, the IoE can be used to achieve public policy objectives, environmental sustainability, economic, and social objectives, etc. The combination of the IoE with Big Data processing in urban spaces is another example that shows great potential. As cities become “smart cities” they will increase their use of the information and knowledge they generate and will be able to address highly specific problems and challenges that citizens have (Miraz et al., 2015).
It must be noted that the IoT is somewhat different from the Internet of People (IoP). The latter uses a PC, tablet, or smartphone and runs apps that connect to a remote server to do something (i.e., browse the web, send an email, shop online, watch video). Unlike IoP, IoT is based on devices that can sense events on their own and, using analytics and business intelligence, respond faster and better than humans. The adjustments and adaptations of those responses are made without human intervention.
13.2 How is the IoT Inside?
To fully understand what the IoT is like on the inside, it is first important to understand how its assemblage works, i.e., how connected objects/devices work together and how the ability to do things at a systemic level emerges that no object could do on itself (Hoffman & Novak, 2015). The IoT is made up of a wide variety of heterogeneous sensors and components, different communication protocols, and processing technologies that resemble the modules of an architecture and interact with each other in three different ways:
Between one component and another (i.e., within the assemblage).
Between one component and the assemblage (i.e., a part with the whole).
Between one assemblage and another (i.e., between assemblages).
Assemblages are not fixed but are constantly changing as new components or modules can be added or removed (Ng & Wakenshaw, 2017), thus forming a network-like structure that is designed to connect whatever “thing” may be identified as an object, capture its data, and process and distribute the information anytime, anywhere (Ma et al., 2013).
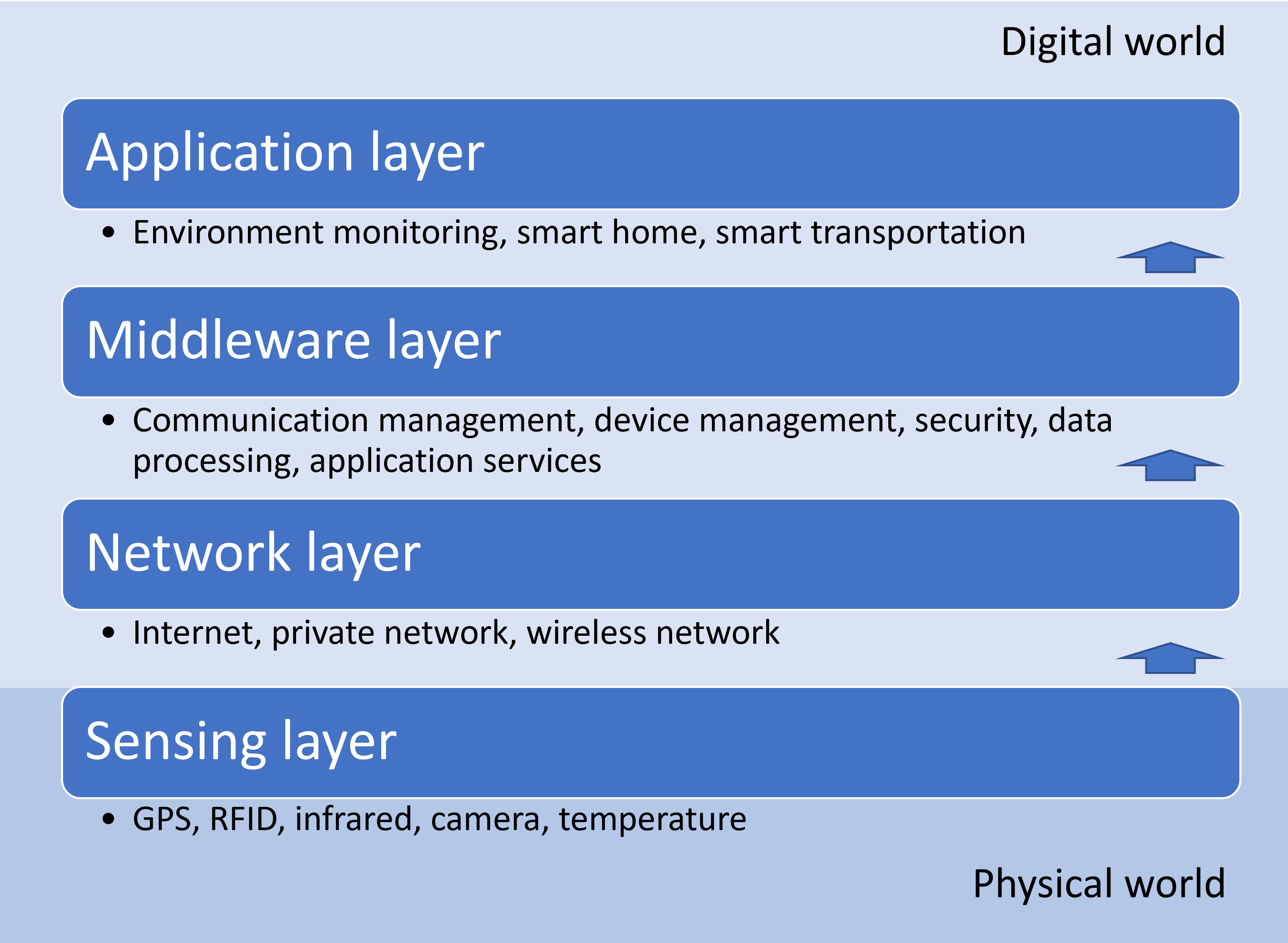
As the IoT is a very broad concept and its components are so varied and heterogeneous, there is no standard and uniform architecture that defines it. This often causes interoperability issues when it comes to integrating all the different types of technologies. To address this problem, the IoT architecture can best be seen as an intelligent multi-layered system that enables the identification, positioning, tracking, monitoring, and management of devices, and the data generated by them. More specifically, architecture based on four layers is the most common in the IoT, as shown in Fig. 13.3 (Attaran, 2017; Ma et al., 2013):
Sensing layer (also known as layer of things) is the layer that connects the physical and cyber worlds. This layer contains the sensor-like devices (things) that collect the information, such as RFID readers, infrared sensors, GPS systems, monitoring cameras, etc. and actuator type things. Through the sensing layer, the IoT assemblage achieves the ubiquitous perception that distinguishes it from other networks, as well as the real-time monitoring and management of the behavioral properties of the objects that comprise it.
Network layer (also known as communication layer, or gateway and network layer) is the layer where things connect (i.e., the medium through which the data collected by devices is transmitted to higher layers for further analysis and processing). This layer consists of an IoT gateway made up of an embedded operating system, signal processors, microcontrollers, and gateway networks like LAN (Local Area Network), WAN (Wide Area Network), Wi-Fi, etc. The gateways route the data that comes from the sensor and the network layers and moves it to the next layer, which is the service management layer. This layer has a large capacity to store data from sensors, RFID tags, etc. and delivers consistently reliable performance across public, private, and hybrid networks.
Service management layer (middleware layer, or data processing layer) is a crucial part of the IoT architecture, as it is responsible for carrying out data and text mining, information processing and analysis, information security, device management, and providing service interfaces for user applications. This data management process is necessary to extract information from the huge amount of raw data collected by sensor devices and to generate a valuable outcome.
Application layer is an interface between the end user and the general IoT architecture that builds on top of the three lower layers to provide end-user IoT applications in various domains. These applications can be as simple as turning off an electrical switch or as complex as monitoring critical infrastructure.
One thing to keep in mind is that IoT layers cannot be created or function independently of one another. Therefore, an IoT solution is not the mere addition of layers, but an integration process that extends to the physical level, and where the whole is greater than the sum of its parts. Furthermore, a well-structured IoT architecture is the foundation that will help firms create innovative services. For this, it is important that the IoT architecture is designed considering the existing technological infrastructure, its scalability, as well as low energy consumption and cost-effective start-up, maintenance, and updating (Ghule & Sakhare, 2017).
Most IoT platforms are designed to support a wide variety of applications and services, but they are different in performance, security, customization, ease of use, and management (Lee, 2019). This is why choosing an IoT platform is not easy and tourism firms need to consider things like scaling and cloud access options, disaster prevention and recovery plans, security and data backup measures, communication protocols and standards, and the type of technical support offered. In addition, firms must decide whether to implement private IoT infrastructure, third-party IoT infrastructure, or a hybrid (private and third-party) IoT. Furthermore, owners and managers will need to assess and decide on the IoT infrastructure (i.e., total cost of the infrastructure related to hardware, software, labor, and maintenance), and on the main qualitative elements, such as the intangible benefits and risks, the level of customization required, and the organizational skills required.
13.3 IoT Data and Processes
Data management in the IoT involves data collection, processing, storage, and analysis processes. In general, IoT data shares these five distinct characteristics (Ma et al., 2013):
Heterogeneity: IoT data is of different types and has very different properties that are used to describe the state of “things”. IoT data ranges from integers to characters, to semi-structured and unstructured data (e.g., audio, video, images).
Inaccuracy: Data inaccuracy is one of the most limiting factors affecting the adoption of IoT. For example, in the case of RFID systems, there are studies that show that only between 60% and 70% of the data can be used, since most of it is unreliable or unreliable. This situation is repeated with other data sources and technologies, which creates difficulties for the direct use of data.
Massive data in real time: The connection of millions of devices and the communication between them through networks generate a huge volume of heterogeneous data that flows uninterruptedly, at high speed, and in real time. Consequently, processing IoT data requires scalable and strong storage, classification, and value creation capabilities.
Implicit semantics: IoT data is data extracted from digital representations of objects with weak and low-level semantics, since it has little or nothing to do with human perception. For firms to build applications up to the level of smart services, data semantics must be abstracted from the mass of low-level data using an event-driven perspective.
In accordance with the characteristics described above, the use of IoT data requires some key processes to be carried out as shown in Fig. 13.4 (Ma et al., 2013).
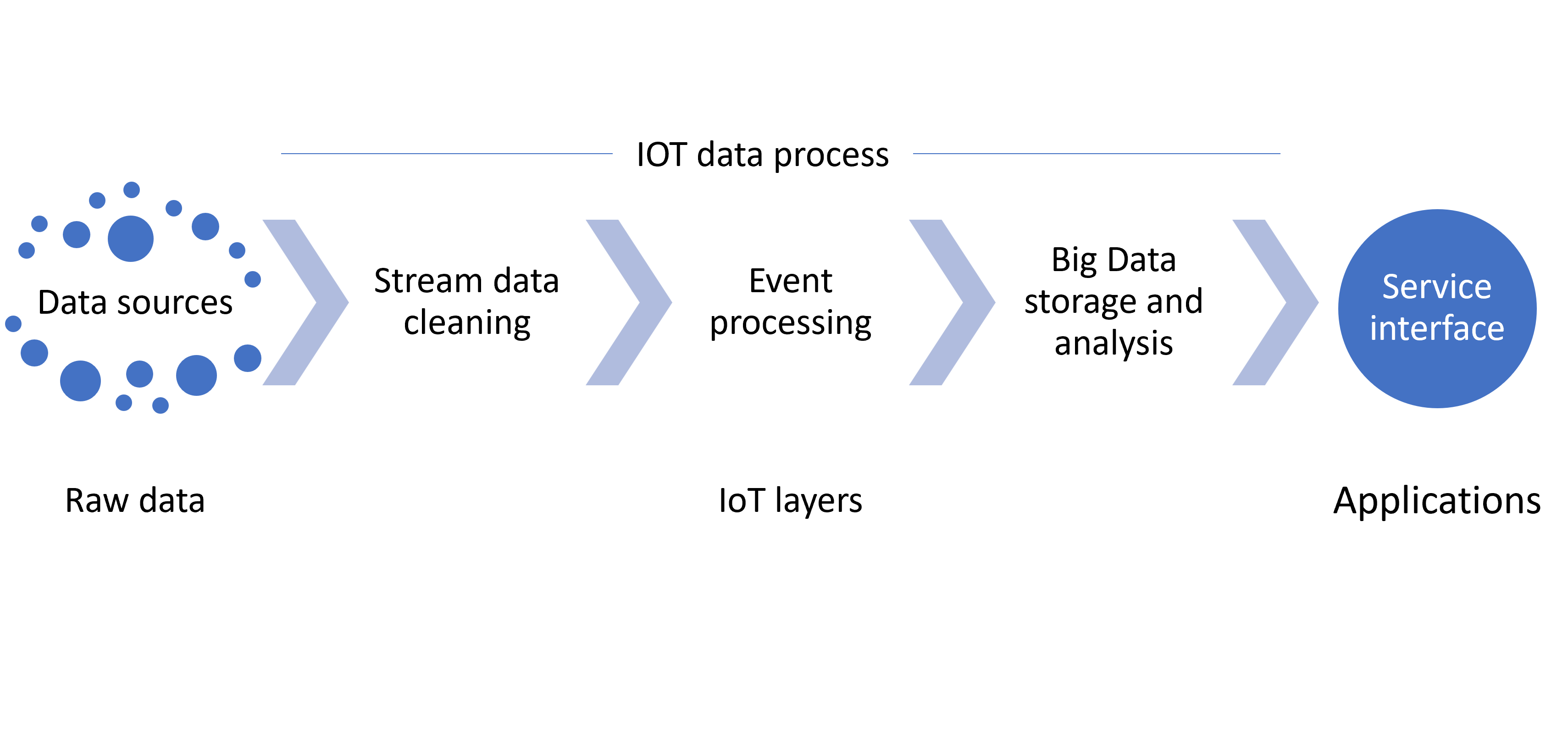
Data cleansing: It focuses on overcoming the lack of reliability that plagues IoT data, which is often incomplete, erroneous, and duplicate. Data cleansing is an essential step for the correct analysis and interpretation of IoT data. Cleansing data is a real challenge for most organizations given the enormous volume of data generated in IoT, the variety of sources and errors that exist, and the need to process it in real time. Once the IoT data is clean, it can be put to use.
Event processing: Clean but still unprocessed data only provides very simple information that cannot be used to support business processes and management decision-making. Firms need to transform this raw data into a high-level business logic that is understandable by users. This is achieved by applying event processing techniques, such as CEP (complex event processing) semantics, which is very similar to the tasks performed by the human brain when trying to recognize patterns in the information it receives. CEP abstracts information by aggregating low-level events into high-level events that make sense to a user and can be responded to.
Data analysis and storage: Once the data has a business logic, the next step is to analyze, store, compress, and exchange it. Data must be able to be shared between different IoT devices and systems; however, this is not always possible due to platforms that are heterogeneous. In this case, it becomes necessary to have a multi-platform information exchange language (similar to XML) that covers different application domains.
13.4 Creating Value from IoT
IoT ecosystems represent an opportunity for business owners and managers to go beyond traditional ways of doing business and create new sources of value. From an internal point of view, owners and managers should see the IoT as an opportunity to reach new levels of organizational efficiency and effectiveness and improve innovation processes, thus generating long-term value for the firm (Lu et al., 2018). By enabling “things” with the ability to be identified, monitored, and encrypted, it is possible to increase the speed, accuracy, convenience, and quality of transactions and processing of products and services.
But, which firms can benefit most from the IoT? Surely it will be those more advanced firms in the data value chain, which have already captured data that requires analysis. Actually, most Big Data analytics vendors already offer solutions to generate new revenue streams from the IoT, such as IBM Watson IoT platform, Google DeepMind, AWS, and Microsoft Azure.
Tourism firms should understand the potential of the IoT for business process management, technology strategy and management and, ultimately, for the design of long-term value creation strategies. They should learn that the main mechanism by which IoT technologies create value is through the generation of refined real-world information, on which they can base the optimization of technological and business processes (Del Giudice, 2016). However, more evidence is needed on how the IoT is changing the way firms manage their core business processes and the impact on knowledge flows, innovation, and competitiveness. A recent survey of 500 business executives who had led IoT initiatives in their organizations asked them to identify which functions were top priorities for IoT (Insights Team, 2017 as cited in Nord et al., 2019). Although the findings revealed that the IoT is affecting many parts of organizations, three areas were identified as priorities:
The first priority area is the customer experience. This is a key area of business management in which other authors agree that the IoT can help in several ways (Gillet, 2018).
⚬ Monitoring and improving customer experience through the firm’s value offerings.
⚬ Personalizing the firm’s interaction with each customer.
⚬ Improving and learning over time through automatic updates of products and services.
The second priority is measuring and monitoring the performance of the firm in real time, so that IoT can support financial decision-making and provide a more holistic view of the firm that complements the data generated by accounting and financial information systems.
The third priority area is tracking and managing firm assets, such as computing devices, tools, vehicles, machines, etc. By using IoT sensors attached to assets, firms can actively track information about their location and condition without the need for human intervention.
The IoT offers a host of hidden opportunities to create value from the huge streams of data it handles. Unlike conventional data sources, IoT devices generate huge amounts of data in real time, allowing owners and managers to quickly act on business processes and service delivery based on the expectations and conditions of the market. Firms can leverage the Big Data resulting from the IoT to perform valuable analytics on consumer behavior, efficiency, and effectiveness of business processes, and the performance of products and services, which in turn can support strategic business planning.
Production systems incorporating IoT technologies can reveal operational inefficiencies in the organization of human work that can be remedied by leveraging the refined insights that the IoT generates (Sestino et al., 2020). The IoT can be used to monitor production, avoid downtime, and rapidly adapt production methods, all of which can make business processes more effective and efficient, speed up cycles for creating new products and services, and reduce costs.
In the field of services, IoT devices such as “Voice Assistant” can be integrated into traditional services (i.e., hotel room service) to improve their planning and delivery quality. Furthermore, smart products and services imbued with IoT can provide insights into how they are used by consumers, allowing firms to quickly adapt to real market needs and increase productivity. Owners and managers can also use IoT data from past events to identify trends and simulate future scenarios using predictive analytics machine learning techniques and process automation. In addition, when large amounts of data about employee activities are available, firms can use that information to better organize human work, simplifying employee effort and enabling customer self-service, which can increase trust and result in streamlined operations and staff empowerment.
IoT technologies are a great opportunity to create stronger bonds with customers and improve consumption experiences. As going online has become the norm, people have become accustomed to consuming personalized services at high speed. Features built into IoT devices, such as voice commands, can satisfy these desires and encourage consumers to think of their devices (e.g., smart watches, smartphones, etc.) as assistants during pre- and post-purchase activities rather than just tools. Promotional strategies, advertisements, and more customer-friendly direct marketing campaigns based on geomarketing and geolocation can be activated thanks to data extracted from IoT devices and applications. In fact, IoT data increases dramatically when organizations consider all the touchpoints they have (e.g., websites, screens, interactive totems, voice assistants, etc.). With all this information at their fingertips, firms can provide value offerings that are based on highly personalized business strategies. These opportunities are further expanded when firms consider the use of AI technologies.
Additionally, the intellectual capital of firms in the form of knowledge, information, and ideas is a crucial element to create value from the IoT. This is because IoT technologies are changing the way firms acquire and manage knowledge inside and outside organizations. Firms should exploit the IoT through knowledge management systems that incorporate advanced ICT and explore external sources of knowledge, which in turn would translate into better and innovative performance. This will drive firms to adopt an open approach to fostering knowledge flows and improving their internal knowledge management capabilities, both of which are prerequisites for increasing the firm’s capacity for innovation (Santoro et al., 2018). When adopting an open innovation approach, firms will need to establish collaborations with other players in the tourism ecosystem to acquire new knowledge and create new value from it. Those firms that first recognize this challenge and approach the transformation process quickly and effectively will be able to gain a competitive edge.
13.5 IoT Technologies
IoT technologies offer the potential to change the tourism marketplace by helping firms develop compelling business strategies. At the organization level, the value created by IoT systems and applications is critical to their adoption and the opportunity to create a new connected world with great potential for firms, consumers, and governments. But new problems and challenges inevitably arise.
One is that IoT technologies have different and often competing standards, which leads to a fragmented market for IoT products and services. The need for a market standard is key because it would lead to network effects (i.e., increasing value to users as more members join), but also because end users, be they home consumers or firms, will continue to be reluctant to invest in systems that they fear will be compromised, become obsolete, or simply are not able to communicate with other IoT devices. It is expected that this trend will normalize in the medium term and that some of these standards (and industry players) will prevail over the rest and begin to dominate the IoT market. Next in this section, the technologies that are playing a more relevant role in the development of the IoT are described (Fig. 13.5).
13.5.1 IoT hardware
At the core of IoT technologies is the link between the physical and virtual worlds. Critical to this is having the right hardware, which can be sensors, microprocessors, RFID chips, and antennas, as well as full-fledged devices like fitness trackers, thermostats, lighting, smart meters, door locks, etc. that are embedded in consumer environments, smart cities, or smart industrial environments (M2M). The main hardware components that form the technological base of IoT systems include (De Saulles, 2016):
Sensors: As a result of the massive adoption of smartphones, sensors that a few years ago were very expensive and only available to a few have drastically reduced their cost and their use has spread, thus facilitating the development of IoT systems. Sensors are not only hardware sensors or sensor networks, but also sensor software. All of them form a system capable of capturing conditions of interest in the real world, such as the presence of people. Most likely, sensors are going to be the main source of data in the future thanks to their high speed, lower power consumption, and high resolution. Common sensors include accelerometers, GPS chips, and cameras.
Smartphones: Smartphones can behave as sensors and controllers for IoT devices through mobile applications (e.g., smart watches and smart home applications).
Processing capacity and bandwidth: The deployment of 3G and 4G cellular networks in most of the developed world, as well as cheap broadband connections for businesses and homes with Wi-Fi capabilities, allow wireless connectivity capable of supporting IoT developments cheaply and ubiquitously.
Big Data infrastructure: Back-office infrastructures put into service by major players in the technology industry have been increasing in recent years. As a result, firms in all industries have powerful facilities at their disposal to store and process the vast amounts of data generated by IoT devices at low cost.
IPv6: The old IPv4 protocol, first implemented in 1983, had a limitation of 4.3 billion unique addresses. In a world in which some analysts (like IDC) predict more than 41 billion connected IoT devices by 2025, capable of generating 80 zettabytes of data, it was essential to develop a new protocol. The new IPv6 protocol provides 3.4 × 1038 addresses, an almost unimaginably large figure, and more than enough to cover IoT needs for decades to come.
The integration of IoT with the cloud (CoT) is another vast source of opportunities.For example, it can help manage IoT resources and provide IoT services more cost effectively and efficiently. In addition, it can simplify the flow and processing of IoT data and facilitate faster installation and integration at a lower cost (Atlam et al., 2018). However, CoT is not straightforward and presents significant challenges for IoT applications that are time sensitive or where internet connectivity is poor and a traditional centralized cloud computing architecture is not possible. In cases like this, a more advanced cloud computing paradigm is needed to overcome latency and capacity limitations.
One of these technologies was suggested by Cisco in 2014 and is known as Fog Computing. Transmitting massive amounts of raw data over a network to a centralized location places a heavy load on network resources. To make this process more efficient, it is possible to process the data close to its source and send only the data that has value to the remote data center. Fog Computing (similar in many ways to what is known as edge computing) processes data as close to the source as possible, so intelligence is transferred from the cloud to the edge. Time-sensitive data (e.g., for connected vehicles, video streaming, gaming, and virtual/augmented reality) is processed at its origin in the edge computing architecture, or sent to an intermediary server located close to the source. Meanwhile, less time-sensitive data is sent to the cloud for long-term storage or historical analysis (Attaran, 2017). With Fog Computing, IoT data processing and storage capabilities can be provided locally on IoT devices instead of being sent to the cloud, so the “fog” offers a higher quality and faster response service. Fog Computing is all in all a good technical solution that enables IoT to provide efficient and secure services for many IoT users.
13.5.2 IoT software
While the hardware is often the most visible part of an IoT system, especially when it comes to our homes or the devices people wear, the software running on the hardware is arguably even more important from a business perspective. Software within the context of IoT is not just limited to the software behind the “things” operating system but includes the applications that manage communications with other “things” and with hubs, the middleware that connects with other applications, and the software that supports data capture and analysis in the back-end (De Saulles, 2016).
Much of the IoT software focuses on processing the data generated by the IoT (i.e., making sense of the data and improving business processes and decision-making). This often requires complex back-end systems to store and analyze the results. The software used for managing conventional databases is often not appropriate for the much larger data sets generated by the IoT. Database software solutions built around frameworks like Hadoop and NoSQL have proven capable of handling massive volumes of data at very high speeds. Other software vendors offer data warehousing and analytics solutions based on these technologies, including the Microsoft Azure platform, GE Predix platform, and Amazon Web Services (AWS). Once data from an IoT system has been captured and processed within one of these data platforms, analysis and visualization of the information is crucial if meaningful decisions are to be made. Vendors offering enhanced data visualization and reporting services include some of the established business intelligence players like SAP, SAS, Tableau, Splunk, or Qlik.
Another key factor for the development of IoT systems is how to make them smarter. This involves uniting IoT with AI. AI can transform the IoT into an entity that works intelligently and behaves with decision-making capacity based on data and past events. By incorporating reasoning and decision-making capabilities into the IoT, the system can automate the management and control of IoT functions autonomously (e.g., self-configuration, self-protection, selforganization, self-healing, self-sufficiency, self-learning, self-adjusting), thus reducing the operating cost (Pramanik et al., 2018). What’s more, the IoT system can automatically train, learn, and fix future problems to a certain extent.
Furthermore, a wide variety of communication technologies covering many domains of application and communication requirements have gradually emerged. Some technologies are domain-specific applications, such as Bluetooth Low Energy in personal area networks or Zigbee in home automation systems. Others, such as Wi-Fi, Low Power Wide Area Networks (LPWA), and cellular communications (such as 3GPP – 4G Machine Type Communications, or MTC) have a much broader reach. These niche solutions are often very dynamic, constantly evolving into new technologies or application domains. The advent of 5G communications means a potentially disruptive factor for IoT technologies. With the expected increase in data speed, lower end-to-end latency, and improved coverage over 4G, 5G is expected to meet the most demanding IoT applications in terms of communication requirements and number of connected devices. Furthermore, 5G may become a unified interconnection framework, facilitating seamless connectivity of “things” with the internet by integrating heterogeneous access technologies (Palattella et al., 2016).
13.5.3 IoT communications
IoT communication technologies include the connectivity technologies, standards, and protocols that connect the IoT to the internet. Connectivity is an essential element of any IoT system as it allows users to control “things” and makes data extractable and manageable remotely. Today there is no single communication protocol or standard that allows the exchange and integration of sensor data across devices, users, and domains (i.e., the data has a meaning that is independent of the device or format in which the information is used). This is because some devices require communication chips that consume very little power and only need to function over short distances, while others are less constrained in their power requirements and need to transmit data many miles away.
The situation has led various technology companies, organizations, and consortiums to work on the development of standards that allow interoperability between devices and systems that are very heterogeneous. Some of them like Bluetooth, Wi-Fi, and GSM are standards already widely used. Others, such as WeMo, ZigBee, and Thread, are used by IoT device manufacturers but have failed to gain a foothold in the market. There are also communication standards, particularly in the 5G environment, that are still under discussion and development and have not been released yet. Finally, to achieve the ubiquitous connectivity that IoT applications require, many more features and functionalities will need to be added to the current broadband approach, which will require new developments, such as the heterogeneous networks (HetNet) approach that allows multiple types of wireless access nodes.
13.6 IoT Applications
Although IoT is in its infancy, the number of applications is growing exponentially as more and more devices gain the ability to connect, opening new opportunities for innovation with smart products and services. Basically, IoT applications can be categorized into two types: consumer IoT and industrial IoT, each with different implications for underlying technologies and business models (Shim et al., 2019).
13.6.1 Consumer IoT
Consumer IoT (cIoT) applications involve the interconnection of consumer devices and everyday “things” located in the users’ environment, be it the home (e.g., refrigerators, televisions, and appliances), the workplace, or even cities, aimed at improving people’s quality of life, saving time and money, and making decision-making easier. cIoT applications interconnect physical “things” through digital means of communication (wired or wireless) and allow them to exchange information with each other to help the user in their daily tasks or make intelligent decisions on their own. For example, in automated homes and buildings, the temperature and brightness of lights can be automatically adjusted according to the context and the presence of people in the room, thus improving people’s comfort. A thermostat in a room and the air conditioner are two “things” that can communicate with each other through IoT, in such a way that the thermostat exchanges the sensed temperature with the air conditioner so that it regulates the temperature.
User acceptance of cIoT technologies and services depends on whether they find it useful and easy to use (Lu et al., 2018). Some studies have also found that fun and pleasure are additional factors influencing the acceptance of IoT technologies and that should be considered when designing IoT products and services. Price is another important factor. Many of the business models of IoT companies are based on subscription models in which users pay periodic fees for the value-added services that the products deliver. Therefore, as long as fee schemes do not share the customer’s logic and are difficult to understand, prices will continue to be a key conditioning factor that affects the rate of adoption by consumers.
Additionally, emerging innovative technologies like IoT often come with risks. When these are known or perceived by users, they directly influence the intention to adopt the IoT. In addition to issues related to privacy and security, the intangibility and intensive use of different technologies in IoT systems often make users perceive higher risks, thus discouraging its adoption. Last but not least, there are the factors associated with social influence (i.e., when an individual believes that someone influential thinks he/she should be using the technology). Social influence is a more important factor than it seems at first glance and can significantly persuade users to adopt IoT. To address this challenge, firms’ business strategies should focus, for example, on offering financial incentives to lead users who recommend IoT products or services to others, as well as encouraging peer-to-peer promotion and diffusion of IoT.
13.6.2 Industrial IoT
Less visible to most users than the cIoT, IoT business and industrial applications (iIoT) have a far greater economic impact than consumer ones (De Saulles, 2016). Indeed, it can be said that iIoT technologies are the real driving force of the socalled Industry 4.0, in which industrial processes and machines become more intelligent and modular, providing greater flexibility to meet customers’ demands.
The iIoT focuses on the integration between industrial technologies (i.e., production and delivery technologies) and ICT, so that the resulting IoT systems can monitor and collect data, and exchange and analyze information to intelligently change their behavior or reconfigure business processes. Some examples of iIoT are hotel process monitoring, vehicle fleet tracking, and beverage vending machine monitoring, control, and replenishment. iIoT has important implications for the management of organizations and their decision-making processes, as well as their ability to create new services and revenue streams. Today, iIoT applications are varied and can be found in all types of activities and industries, from public services, to transport and logistics, manufacturing, smart cities, smart buildings, industrial automation, and tourism, where they can improve the productivity and save costs through process optimization.
By collecting and analyzing IoT-based Big Data with data analytics, firms can enhance their understanding of consumer behavior and decision-making, including predicting what is going to happen, all of which has relevant implications for marketing management, innovation, and the management of business strategies. This explains why tourism firms should start equipping themselves with infrastructures and new capacities that allow them to process and analyze the Big Data generated by the IoT (Jesse, 2018; Sestino et al., 2020).
Both cIoT and iIoT applications share common features and have clear differences. For example, communications in cIoT are from machine to user (client–server type) and seek that the connected “things” have low energy consumption and are easy to install, integrate, and maintain. On the other hand, iIoT applications use machine-to-machine communications for automation and/or monitoring of control processes. Additionally, cIoT and iIoT specific communication requirements often differ in terms of reliability, quality of service (i.e., latency, throughput), and privacy protection (Palattella et al., 2016).
Marriott International has partnered with companies such as Samsung and Legrand to develop a smart hotel room. The project aims to improve the guest experience through more efficient room design and construction, thereby contributing to Marriott’s sustainability goals. Some of the expected benefits of the smart room include guest access to their own data and information, voice- and mobile-controlled systems, and enhanced personalized service. The project features various IoT systems, devices, and applications for device-to-device communications. Samsung develops end-to-end IoT services from intuitive lighting to voice-activated room controls powered by the ARTIK platform and SmartThings Cloud. Legrand offers a suite of power, light, and data solutions that bring power and connectivity to previously untapped locations. Marriott has well-established private data centers that extend into the public cloud and more than 20,000 devices are equipped with enterprise mobility management software that ensures its mobile workforce can reliably serve customers anytime, anywhere. IoT-enabled building management, room management, energy management, and lighting control software and hardware reduce the environmental footprint of water/carbon/food waste and contribute to the general goal of reducing the environmental footprint.
Source: Source: Own elaboration based on Lee (2019)
13.7 Challenges of IoT
Before the IoT can reach the levels of adoption seen with other technologies, there are a number of significant barriers and challenges that need to be resolved, and they are not just technical. As ICTs become more and more integrated into our daily lives, at work and at home, so do the challenges and potential adverse consequences, such as theft of sensitive personal data from devices, or hacking of IoT systems in industrial settings to take control of power supply systems. The controversial “always on and listening” IoT encompasses a growing range of devices. Google’s “Ok Google” search command for smartphones and PCs, Apple’s Siri, and Amazon’s Alexa are examples of how tech companies are trying to make their digital assistants a natural part of our daily lives. As machine learning and voice recognition improve, they will become even more integrated into our homes and the amount of data that can be coveted by criminals will grow.
Due to the rapid growth of the IoT industry, the demand for professionals with the necessary skills to create IoT-enabled devices and manage the layers that make up the IoT architecture has increased exponentially. Firms need staff with high-level technical skills in today’s programming languages who also understand the business environment and infrastructure in which IoT devices operate. Software developers are always in high demand, but the growth of IoT will increase that demand even more.
In many ways, these challenges are nothing new. In fact, we have seen similar challenges arise in the life cycle of other technologies, such as when the internet or personal computing began to grow. However, it is the sheer scale of what the IoT promises that raises concerns among consumers, firms, developers, and regulators. Below are some of the main challenges affecting IoT adoption, including IoT Big Data, privacy and trust, security, regulation, and business models.
13.7.1 IoT Big Data
IoT systems generate a large amount of data that comes from highly dispersed and heterogeneous sources. For firms this means a great challenge, since they must deal with a large variety and noise in the data. Added to this is the fact that conventional data mining algorithms are not ready for Big Data, therefore the problem of how to modify them to operate in a Big Data environment arises. In this challenging context, it is especially important that firms develop a Big Data mining framework that is efficient and effective for exchanging data between different applications and systems, and that guarantees data security and privacy.
13.7.2 Privacy and trust
People are increasingly concerned about how firms use their personal data. Despite the many applications and benefits that IoT can have in everyday life, if privacy concerns become too great, consumers may lose their willingness to interact with IoT platforms and business opportunities will not arise. This situation becomes even worse when we think about the dispersed nature of the IoT and location-based or geo-referencing tools. Personal data has become a new “asset class” that can create value for individuals, firms, and society. As the volume of data grows, firms must take steps to encourage the kind of trust that fosters privacy, increasing the transparency with which personal data is used and balancing business interests with user privacy concerns (Sestino et al., 2020).
Blockchain technology can help overcome some of these obstacles by providing a solution for authenticating the identity of nodes in an IoT network and verifying that only authorized nodes can access data, thus maintaining data privacy and access control (Shim et al., 2019). IoT devices could send data to a blockchain-based database that would only allow authorized parties to access and contribute data without the need for centralized control and management. Eventually, the combination of IoT with blockchain can reduce the privacy and security risks of IoT data and turn it into a trusted source of valuable data. These benefits could also be extended to the management of payments in the form of micropayments that would help monetize data from IoT networks. For example, hotels could send information about the flow and characteristics of visitors to visitor control centers, then this data could be traded (or auctioned) on Big Data marketplaces to facilitate analysis, marketing, and market research as value-added services. In summary, the convergence of IoT and blockchain is at a very early stage and still offers numerous technical challenges given the immature state of these technologies and the speed at which they evolve, however it is worth keeping an eye out for further developments.
Ultimately, firms are expected to develop new trust models especially focused on 5G scenarios where there will be a huge number of different devices connected, each with its own security scheme. This will raise new expanded requirements for authentication and protection of personal data between different actors that will reinforce those currently used for 4G. Furthermore, firms will be required to develop new ethical practices in the handling of personal data that involve users in the process. These practices will be critical for people to gain a high level of confidence in using IoT, and include issues such as data ownership, accessibility, and accuracy. At the same time, it is to be expected that as people get used to new IoT environments and realize its benefits, some privacy concerns will diminish and people will gradually become more willing to share their personal data.
13.7.3 Security
Wherever a technology can be used to exploit a weakness in a system for profit, it is inevitable that someone will take advantage of it. In other words, if a system can be hacked, it will be hacked. Being aware of this maxim, security has become a primary concern for firms focusing on adopting IoT. IoT technologies open the doors of firm systems and data to everyone and increases security threats. Leakage of personal data through illegal hacking has become commonplace, and until reliable and secure systems are in place, many people will be reluctant to share their data with third parties. Interestingly, it often happens that firms that have been hacked never know, or underestimate, the scope of such illegal attacks. In 2012, it was thought that 6.5 million passwords from the LinkedIn social network had been stolen. However, it was only in 2016 that the company revealed that more than 117 million passwords had been taken and that this data was being sold on the internet.
IoT-enabled devices are vulnerable to hacking, and it is feared that they are an opportunity for hackers to steal data and harm people. These risks are further heightened as there is no government regulation of IoT and no organized effort by manufacturers to make these devices more secure. In addition, as firms increase their use of AI, machine learning, and increasingly sophisticated algorithms to give their products and services a competitive edge, the amount of personal and sensitive data circulating on the internet will increase. So, what can firms do to ensure that people’s personal information is secure? Incorporating strong security at all levels of IoT is crucial to preventing fraud and building the necessary trust among users for mass adoption. It is the responsibility of owners and managers to implement methods to protect information in business systems and in interactions with customers. It is also essential that security is built into products and services at an early design stage and not as an afterthought. IoT vendors have addressed some of these security challenges by testing a variety of query protocols, jamming, and other techniques (Attaran, 2017). The Federal Trade Commission of the United States of America also makes these recommendations to firms that want to take their first steps in the IoT (FTC, 2015).
Conduct a privacy and security risk assessment.
Minimize the data collected and retained from IoT initiatives.
Rigorously test IoT products before launching them on the market.
Any firm developing IoT products should seek to maximize the strength of its security strategy. This means thinking about security from the customer’s perspective (i.e., in terms of what the solution will do, who it will report to, and how data will be protected), as well as applying a multi-layered approach that incorporates identity, access, encryption, and network security and monitoring. It is also important for firms to set up the controls that will govern the management of the IoT system throughout its life cycle, how issues will be resolved, and when the system will be retired and upgraded.
There is no doubt that security is more of an issue in some scenarios than others. Hacking someone’s smart thermostat and turning off their home heating can be inconvenient, but taking control of a self-driving car and crashing it on purpose is something quite different. Another concern with IoT security is the number of new firms entering IoT with no security background. For example, a small business that has amassed experience designing and marketing tours of historic places probably doesn’t have the knowledge or skills to create products that can resist hackers. Therefore, new technologies and methodologies must be developed that meet the highest requirements in terms of reliability security, and privacy, and that can be adapted to the particular needs and capabilities of tourism firms.
13.7.4 Regulation
A prerequisite for IoT to become a practical reality is building trust among users. As with other ICTs, regulators play an important role in establishing legal frameworks that allow firms to operate with confidence and deliver trust to users. In some cases, new regulations are going to be required that take into account the new challenges posed by the IoT; in other cases, the existing regulations may be sufficient or simply require an update.
Today most IoT regulatory frameworks are still very vague or non-existent. There are also clear differences in regulations concerning personal data between the two world leaders in this subject: the US and Europe. In 2016, the European Commission adopted the General Data Protection Regulation (GDPR), which included some modifications related to data portability and the “right to be forgotten” that recognized how much technology had evolved since the 1990s. The European regulation states that when data is kept in a “structured and commonly used format”, individuals have the right to request that it is transferred to another service provider. Meanwhile, the United States has a more fragmented approach with a series of specific federal and state laws, each addressing different aspects of personal data. This reflects the importance of state legislation in the United States, but perhaps a more relaxed attitude among many US citizens regarding how organizations use their personal data. The lack of regulatory consistency between Europe and the United States with respect to data protection has also been a source of friction with some EU member states due to the restrictions placed on firms operating in these countries and the extent to which they may move personal data outside the European Union. The data protection directive and the GDPR allow the movement of data to firms in the United States as long as they are subject to the same data protection treatment that they have in Europe. Furthermore, IoT has also become the topic of power politics due to the risks of war and cybercrime.
Although there is no clear consensus on how to legislate on privacy, privacy protection policies should guarantee a series of key principles, including data anonymity; notification to users when information leaks and privacy violations occur; that the data collected is treated with the sole purpose of providing services; transparency in data collection; and accountability of data collectors (Lu et al., 2018). Especially challenging is the massive collection of data in the IoT. Soon it will be almost impossible for a person to avoid being monitored and recorded by sensors in public spaces. What’s more, once this information is generated, it may be retained indefinitely, and its disclosure may not be controlled on a personal level. Therefore, when designing IoT applications, information protection becomes critical as it directly affects the user experience and trust in IoT services. The implementation of functions such as “forget me” by service providers, which allow user information to be deleted on request, may be a possible solution to this problem.
In the same vein, there is the issue of security in access to personal data and the problems with organized crime and cyberterrorism. Due to its connected nature, the IoT generates a large amount of data that is collected and transferred between the virtual and physical worlds, and this can be a never-ending source of security problems. Some studies suggest that 70% of IoT devices are vulnerable due to lack of encryption, inadequate software protection, insecure web interface insecurity, and insufficient authorization levels. Furthermore, security threats appear at every layer of the IoT architecture making it even more difficult to analyze security issues, such as phishing and routing attacks, viruses, trojans, and spam messages in data transmission, to name just a few. In the end, solutions to IoT security issues need to involve multiple stakeholders, making it clear who is responsible when a system fails or is attacked by cybercriminals. Improved accountability in IoT (i.e., the obligation of each person responsible for the layers of the IoT system to explain and justify their actions and decisions to users), reinforces security and confirms the need for a stable legal framework for all firms.
13.7.5 Business models
The IoT can impact the business models of tourism firms, both by transforming traditional business models and creating superior value, and by leveraging new business models based on new competitive advantages. IoT-based business models can help improve knowledge sharing by providing firms with a wealth of contextual information about their customers and product/service usage patterns. This abundant knowledge is highly valuable in business terms to increase the innovation capacity of organizations and create new value (i.e., facilitate the decision-making and marketing process, engage the consumer, set prices, etc.). IoT provides opportunities for tourism firms to design new strategies, optimize their business process flows, and offer personalized products/ services to customers (Lu et al., 2018). In short, IoT-based business models can improve the firm’s competitiveness by better satisfying its customers in the product/service delivery process.
Two new but powerful IoT-specific business models have recently emerged: 1) digitally loaded products, and 2) Sensor as a Service (Fleisch et al., 2015). The idea of digitally charged products is that classic physical products are loaded with a package of new digital services based on sensors, so that they acquire more relevance based on new value propositions. One usual approach to this business model is the physical freemium model, which refers to a physical product that is sold at a very small margin together with a free digital service (i.e., a product that is sold with some digital instructions for installation, operation, and maintenance). Over time, customers can activate (purchase) more digital services based on their needs, thus delivering higher margins to providers. Physical products can become a kind of repository for electronic services as they can embed digital advertising, accrue and redeem loyalty points, and record what is happening around it through a smartphone. For example, the Amazon app already offers features like these for products with an Amazon barcode.
The Sensor as a Service model provides the ability to collect, process, and sell sensor data for a price. This model is based on the idea that measured data from the physical world no longer needs to be vertically integrated into a single application, but can be integrated into a wide range of applications. Unlike the digitally uploaded product business model, the focus here is not the product that generates data or the resulting services, but the data itself. An example of this business model is Streetline (http://www.streetline.com), which installs sensors in municipal and private spaces to detect free parking spaces and then sells the collected data to interested third parties.
A drawback when developing IoT-based business models is that for each IoT-based service, several different parties must cooperate (and thus receive benefits) to support the technology and standards that the service requires (Shim et al., 2019). As IoT devices become cheaper and their complementary software services mature, new applications and business models will emerge based on the data they generate.
13.8 Discussion Questions
What type of IoT products and services have the greatest potential for the tourism consumer-oriented market (B2C)? And for the business-to-business (B2B) market?
What relationship is there between the development of IoT, Big Data, and AI technologies? Is it realistic to foresee an integration of these technologies in the future?
What factors related to privacy, security, and regulatory issues are most influencing the development of IoT in the market?
What factors may be having an impact on the adoption of IoT-based technologies and services by the end consumer? And by firms?
What professional profiles are most needed by tourism firms to benefit from the IoT? Does the tourism firm have them?
What management practices should the tourism firm implement to accelerate the adoption of IoT technologies in the organization?
What role does business leadership play in the adoption of IoT technologies in tourism firms?